The digital transformation is a crucial step towards enhancing productivity, agility, and competitiveness in the digital era. Endian, a leading provider of cybersecurity solutions, empowers organizations to securely and effectively transform their IT and OT systems. This article sheds light on the challenges, opportunities, and solutions associated with the digital transformation process.
Table of Contents: What awaits you in this article
Challenges and Solutions for Seamless IT and OT Integration
IT und OT müssen gemeinsam betrachtet werden. (Foto: Envian)
The integration of IT and OT systems is a complex task that requires careful planning to ensure both security and operational efficiency. These systems often operate in silos with different technologies and protocols, making the creation of seamless connectivity challenging. Additionally, the interweaving of IT and OT exposes organizations to increasing cybersecurity risks. To protect critical infrastructures from cyber threats, robust security measures and proactive strategies are necessary.
Challenges and Solutions: Modernizing Legacy IT and OT Systems
Many organizations still rely on outdated IT and OT systems with long lifecycles. Modernizing or replacing these systems requires strategic planning to minimize disruptions and costs while ensuring compatibility with modern digital technologies. Additionally, the shortage of qualified professionals who possess both IT and OT skills complicates digital transformation initiatives. Recruiting and retaining talent capable of implementing and managing integrated solutions presents a challenge.
Ensuring Compliance with Industry Regulations: Endian’s Tailored Cybersecurity Solutions
Compliance with industry regulations and norms is crucial for companies in terms of cybersecurity. Meeting these requirements necessitates robust security measures tailored to both IT and OT environments. Endian facilitates compliance by providing reliable cybersecurity solutions customized to industry needs.
Endian’s Comprehensive Cybersecurity Solution for IT and OT Environments
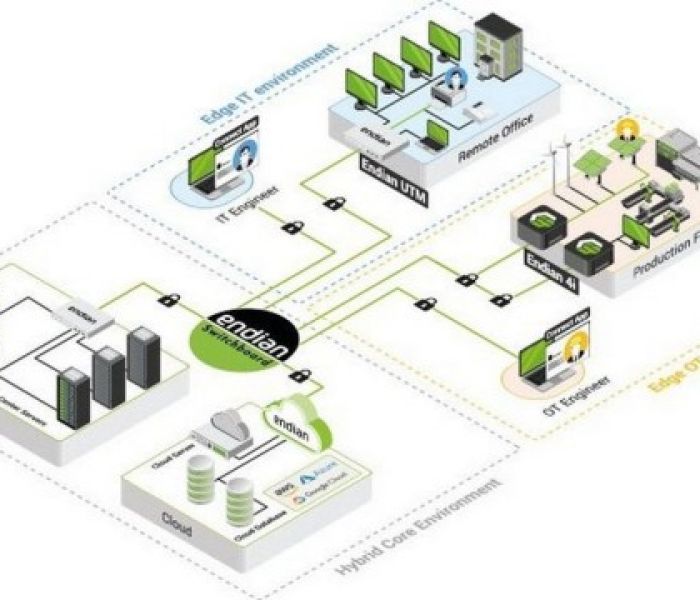
Endian’s comprehensive cybersecurity solution is designed to cater to both IT and OT environments. This platform provides reliable protection, efficient management, and policy compliance all in one. Its key components include a Zero-Trust architecture, secure remote access, device management and automation, unified threat management, visualization of decentralized networks, edge computing, and compliance solutions. With Endian’s holistic approach, businesses can ensure the security and continuity of their operations in today’s digital landscape.
Protecting IT and OT Systems: Ensuring Data Security and Integrity
Securing IT and OT systems is crucial for ensuring the confidentiality, integrity, and availability of important data and processes. Effective cybersecurity measures are necessary to protect these systems from dangerous attacks that can disrupt operations, compromise sensitive information, and even threaten public safety.
Endian’s Unified Cybersecurity Platform: Meeting IT and OT Security Demands in Digital Transformation
Endian’s Unified Cybersecurity Platform is a one-of-a-kind solution that effectively addresses the security requirements for both IT and OT systems in the digital transformation process. By prioritizing cybersecurity, businesses can ensure the confidentiality, integrity, and availability of critical data and processes. Endian’s platform provides comprehensive protection, enabling organizations to successfully navigate the challenges of the digital landscape while maintaining business continuity and trustworthiness.
Ensure uninterrupted business operations with Endian’s integrated solutions. Our comprehensive approach to cybersecurity provides reliable protection, enhances productivity, and instills trust in today’s digital landscape. With our solutions, you can safeguard critical assets, mitigate risks, and maintain business continuity, giving you peace of mind in an ever-evolving threat landscape.